There are different type of standards:
- International Standards, such as IEC and ISO
- National Standards, such as NEN, BS, etc.
- Industry Standard, is not really a standard but a specification that can be shared
The purpose of a standard could be to have a specification that everyone can use, such that products will have a certain level of quality, or can be changed out for another product, to improve the use of it, or to make it possible to interface or connect to a certain product.
The best Standards are International Standards that will be applied globally and the worse Standards are Industry Standards, that do not represent any quality. Industry Standards could, in a worse case scenario, promote bad quality products for commercial reasons. But there are also good and useful Industry Standards, e.g. API, ISA, Namur, etc.
For OT Cyber Security there are several International Standards, although this is a slow moving process. In general it takes 5-10 years to create a new Internalional Standard. The IT world is a very fast changing world and everyday new products are released. Especially now with the IIoT and Industry 4.0 on the agenda the Automation world is facing many changes, such as computing and data storage in the Cloud. The landscape is changing so fast that the Standards cannot keep up.
But there are a few good International Standards that can be used for Cybersecurity that will have an positive impact:

TAPS is very proud to state that the majority of the IEC 62443-2-4 was created by Ted Angevaare, while working for Shell. The Standards was first issued as a Shell DEP (Shell Standard), next as a WIB Report, M2784 and later adopted by the IEC. When the IEC 62443-2-4 was issued the WIB report was replaced/withdrawn, not to create any conflict.
Another set of great Standards are published by NIST (Part of US Department of Commerce). Although available in many languages and used internationally, the NIST Standards and Framework are seen as National Standards.
- NISTIR 8183A Volume 1, 2019
- MISTIR 8183A Volume 2, 2019
- MISTIR 8183A Volume 3, 2019
- Other valuable NIST Standards, e.g. NIST 800 series, e.g. SP 800-82 rev2, 800-53 rev4
Many people promote the ISO 27,000-series of standards. These are great standards, but not suitable for the industry. A study performed by the WIB has demonstrated that less than 50% of the requirements stated in the ISO 27,000 Standards are applicable in the OT and a lot is missing. This is caused because the priority setting in the OT and IT is mirrored and in the OT the Safety aspect is overarching all priorities. Process Safety is not a subject in the IT. Due to these differences the approach and requirements are in the OT are different and this is realised in the IEC and NIST Standards (OT) and not in the ISO Standards (IT).
Another good set of standards have been created by the French Network and Information Security Agency, the ANSSI.

ANSSI Classification Method and Key Measures
As a National Authority, ANSSI reports to the General Secretary for Defence and National Security (SGDSN) and is a government organisation.
ANSSI has created a few excellent National Standards and one of these is a Risk Assessment method, in which also Criticality has been addressed. Criticality could refer to Safety, but also to the other priorities used in Risk Assessments, such as Integrity, Availability and Confidentiality. The standards have been written to address the industry in a wide form, to include the air-craft industry, the car industry, but also other industries such as Oil & Gas, food, water, etc.
Companies in the Netherlands that can do such a TRA (Threat and Risk Assessment) or RVA (Risk and Vulnerability Assessment) and have a proven track record are:
- Magion, The Hague
- Applied Risk BV, Amsterdam
- Hudson Cybertec, The Hague
The ANSSI Standards are:
- Classification Method and Key Measures – Cybersecurity for Industrial Control Systems
- Detailed Measures – Cybersecurity for Industrial Control Systems
This ANSSI Risk Assessment methodology will address 283 subjects over 3 Criticality classes like:
- Securing the ICS architecture,
- Incident response,
- Roles and Responsibilities,
- Access,
- Crisis Management,
- Obsolescence Management,
- Monitoring Process,
- Management of modifications and changes,
- Audits and Cybersecurity tests,
- Integration of cybersecurity in the various phases,
- Integration of Cybersecurity in the ICS life cycle,
- Awareness and Training,
- Documentation Management,
- Back-up Management,
- Risk Analysis,
- Mapping,
- User Authentication,
- Authentication Management,
- Wireless communication,
- Protocol Security,
- Configuration Hardening,
- Vulnerability Management,
- Management of Removable media,
- Security for programming consoles,
- Engineering stations and Administrative workstations,
- Events logs,
- etc.
Another methodology is proved by IEC 62443:
ISA/IEC-62443-3-2: ‘Security Risk Assessment and System Design’ is still under construction and in reviews the statement is made that this method is high level Risk Management. It’s actually a very short document and quick read with about 5 pages after you strip out the formatting and definition sections and an example annex. Therefore this methodology is not recommended by TAPS, although based on an International Standard.
Some End-Users and Security Specialists/Service Providers have developed their own ‘Risk Assessment methodology and Gap Analysis’, but it is better to use the ANSSI method, a method with a respectable reputation!
Knowing your risks, the impact and your gaps is just one of the steps to take and forced by Governments for certain vital industries. Another step is to implement mitigations to eliminate or reduce the impact of the Cyber threats.
TAPS has developed a method to conduct a Cybersecurity project and 37 steps have been defined, of which 12 steps are basic (will create 75% mitigation) and 25 steps ( will create 25% mitigation) are based on a Risk Assessment:
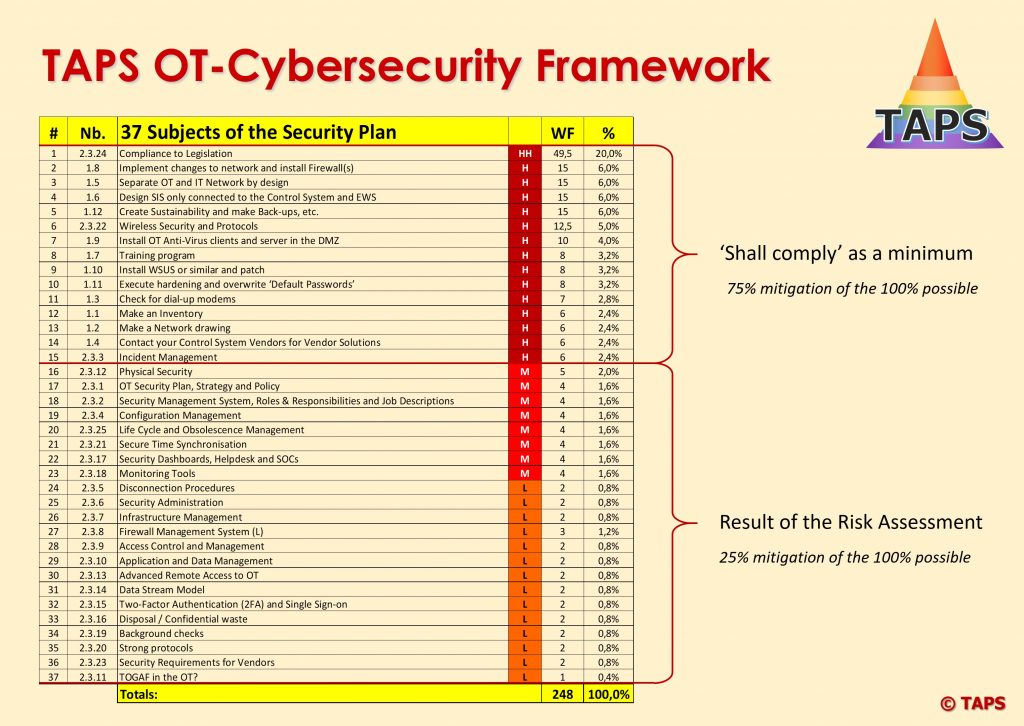
Number 22 and 23 (Security Dashboards, Helpdesks and SOCs together with Monitoring Tools are evolving fast and are now rated with a Weight Factor of 8, representing a mitigation percentage of 3.2%, mainly because these are reactive and not proactive. But some attacks are well planned and malware is injected well before the attack will take place. In these cases the Security Dashboards, Helpdesks and SOCs together with Monitoring Tools are the way forward to prevent an attack at an early stage. It is also expected that IDS (Intrusion Detection Systems) will change into IPS (Intrusion Prevention Systems) in future and then attacks will be stopped at the front door. But today these solutions are not fast enough without creating too much delay on the data stream (minimum of 5 minutes). There are no standards available in the world of IDS and IPS and the Manufacturers of these applications are in a competition battle with each other to create the best and fit-4-purpose solution.
There are many Frameworks possible and another well known Framework is the NIST Framework:
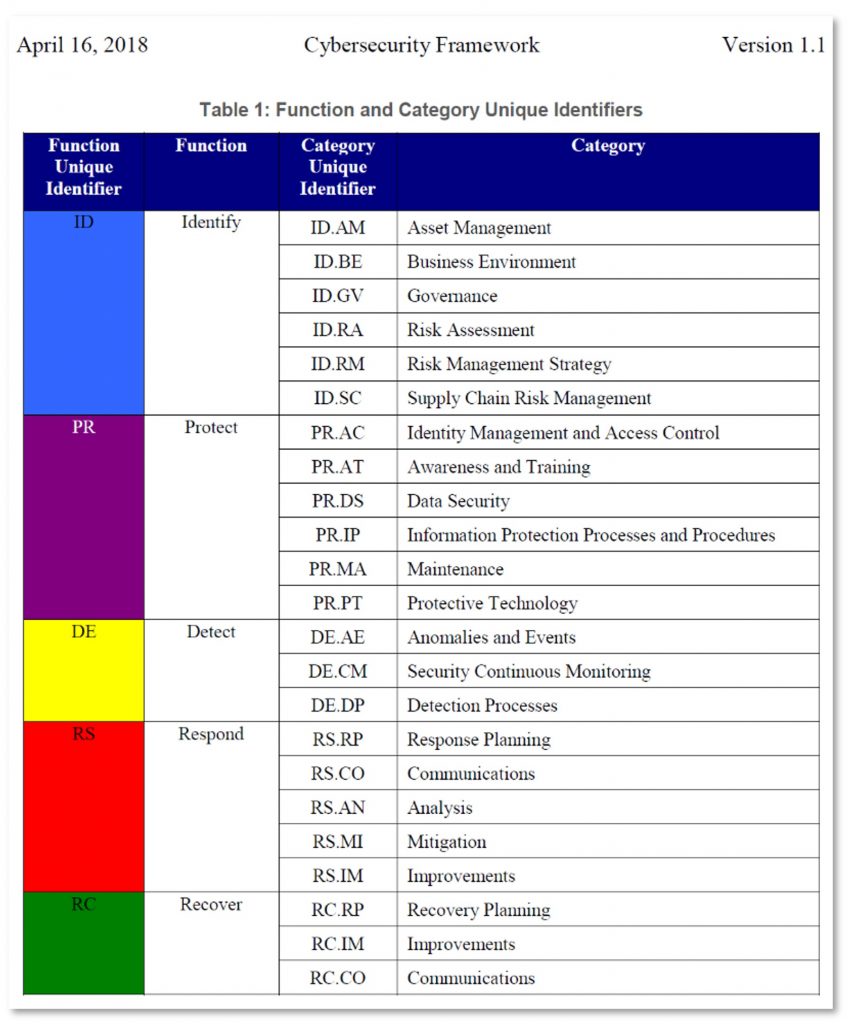
The NIST Framework requires more work before an End-User can start with an implementation project and is a step away from a direct start, when compared to the TAPS Framework. Nevertheless it’s a great methodology and useful for OT Service Providers and OT Cybersecurity Specialist to study and can be used as a reference in audits and reviews, but the TAPS Framework would be the way forward and should be used.
IEC is starting with a new International Standard, i.e. the IEC 62443-2-5: Implementation Guidance for IACS Asset Owners. This standard is in a very early stage and it will take years before this standard is mature enough to be used for implementation/projects.For some Industries the ‘Cost and Impact Effective’ Security Program is not good enough. Think about the nuclear industry and banks. The Nuclear Industry has extensive Cybersecurity regulations in place already since 2002 and more after 9/11.
These industries should investigate in detail all what’s possible and create a model with more than 2 levels of defense to each threat that may occur. To make this visible the Bow-tie model can be used (used in Process Safety):
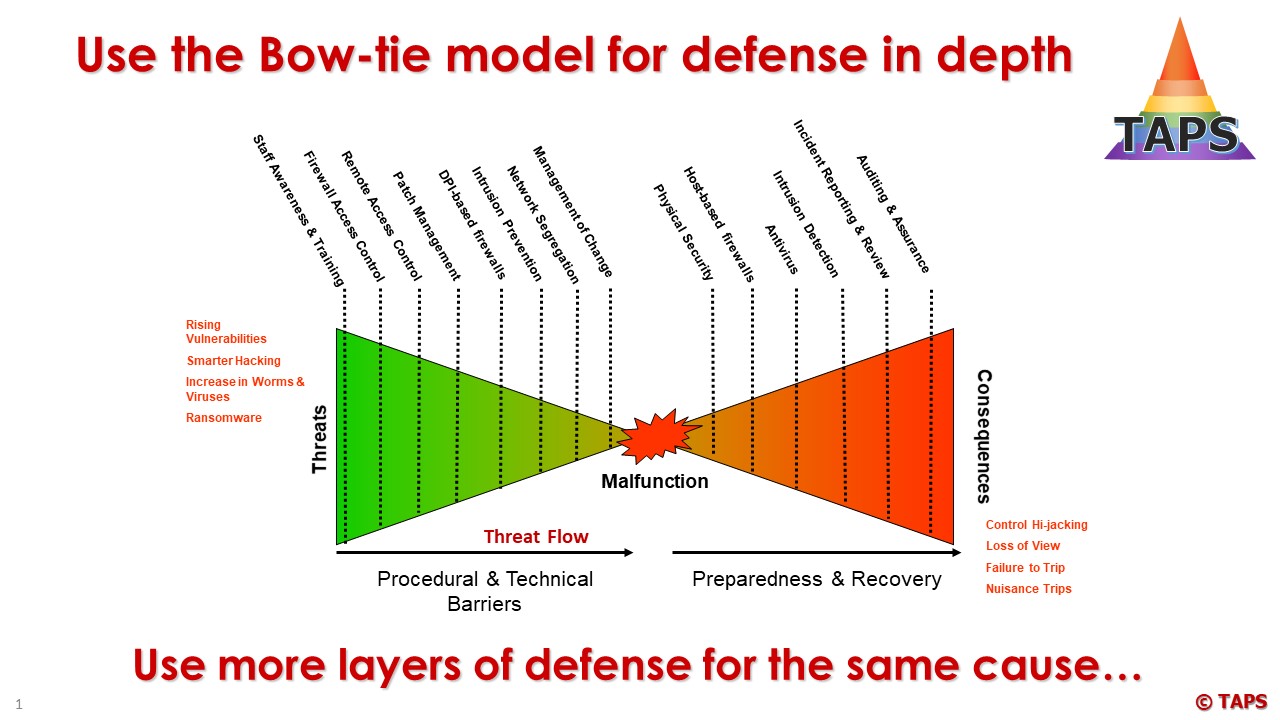
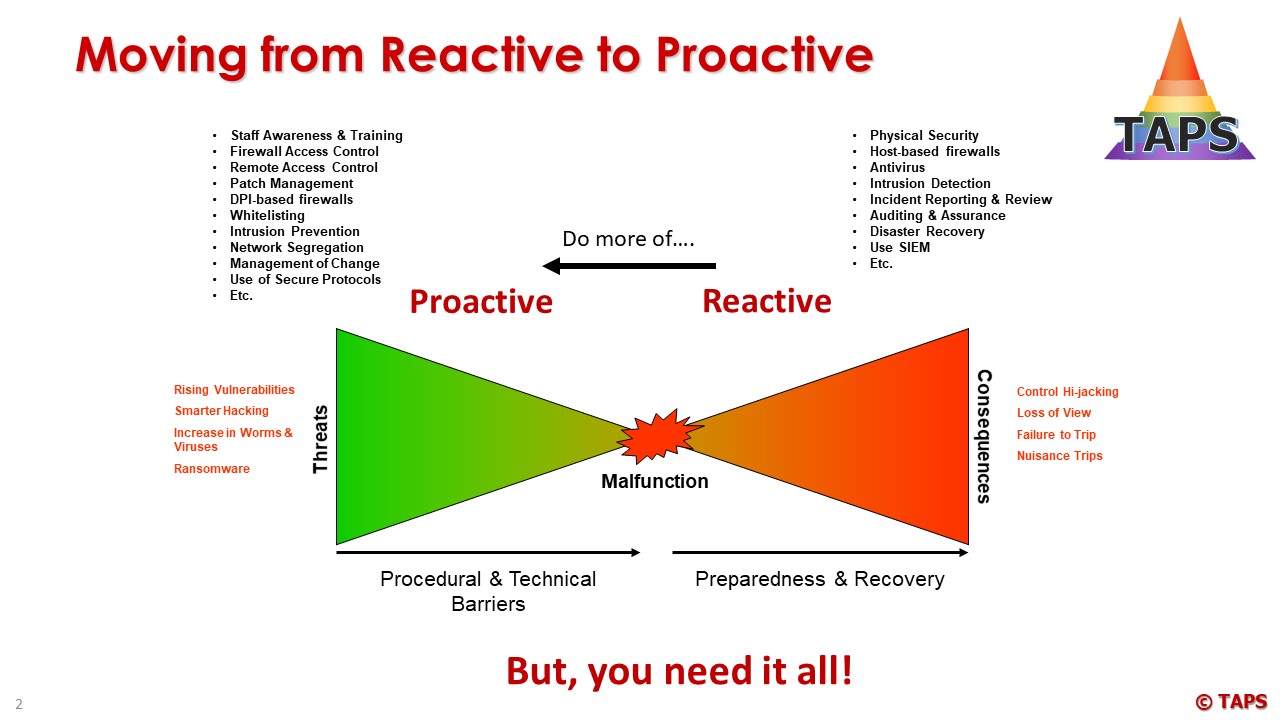
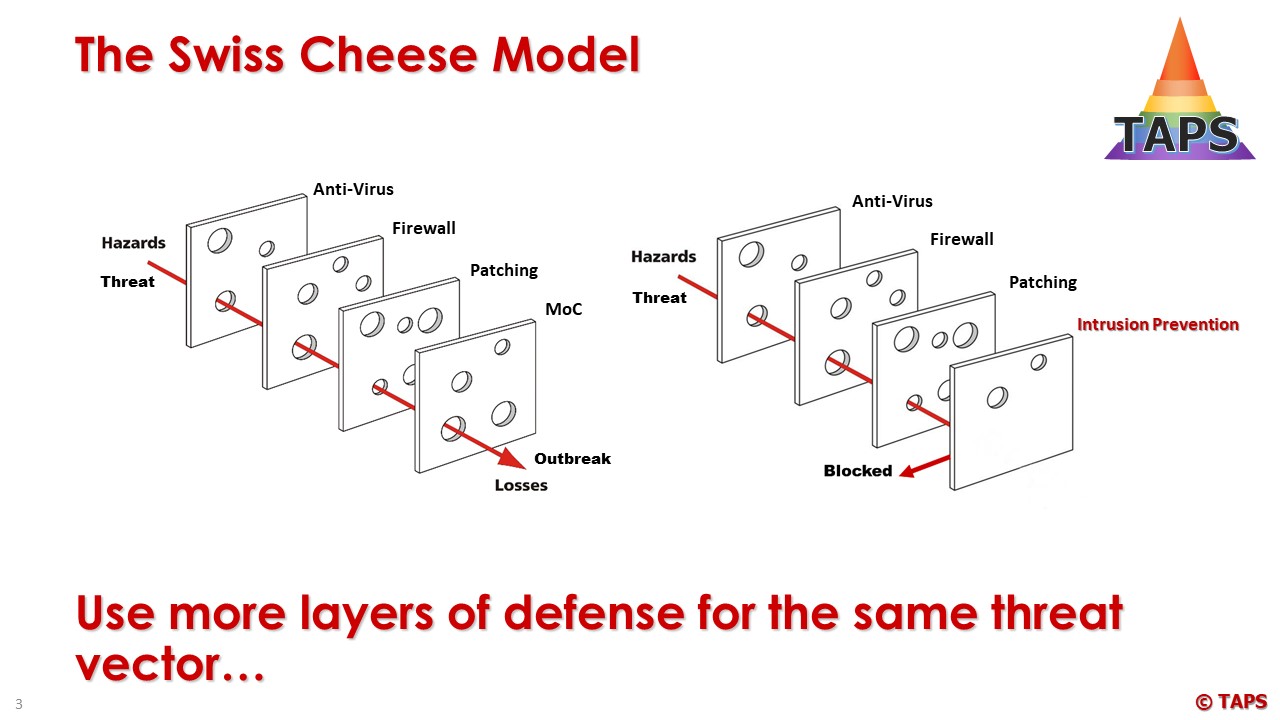
There are no standards available to describe the ‘Maximum Possible’ and End-Users will need to depend on Independent Consultants to inform them on the next steps.