A Cyber-attack can vary from stealing information up to a destructive attack, from cyberwarfare to cyber espionage, from stolen Email addresses to stolen credit card and financial data.
The Industry is most concerned about Malware or Cyber-attacks may change the Technical Integrity (Process Safety) of production facilities. Also data integrity or application function integrity (I) could disrupt or damage the production process or that it may stop the production process, the availability (A).
The PS and CIA priorities are applied:
- PS = Process Safety
- C = Confidentiality
- I = Integrity
- A = Availability
2010 Stuxnet (PS, I and A):
The first destructive attack in industry was Stuxnet in 2010, a malicious computer worm believed to be jointly built by an American-Israeli team that created a cyber weapon. Designed to sabotage Iran’s nuclear program with what would seem like a long series of unfortunate accidents, i.e. centrifuges damaged due to overspeed. The attack caused a set-back of the nuclear program by 1-2 years.

2011 Duqu (C):
Duqu uses the part that have been developed as part of Stuxnet and looks for information that could be useful in attacking industrial control systems, such as stealing digital certificates and corresponding private keys. Duqu’s objective is not to be destructive, the known components are trying to gather information. The target of Duqu again is Iran.
2012 Shamoon 1 (A):
Shamoon 1 is an attack on the oil and gas company Saudi Aramco and wiped out 35,000 computer systems on 15 August 2012. One week later RasGas experienced a similar Cyber-attack. The malware stole information and then destroyed data and computer operation and is seen as the “Biggest hack in history”. Shamoon caused the company to spend more than a week restoring their production.
2013 Havex (C):
Havex malware, also known as Backdoor.Oldrea, is a RAT (Remote Access Trojan) employed by the Russian attributed APT group “Energetic Bear”. It includes an OPC (Ole for Process Control) scanning module, used to search for industrial devices on a network. Havex is known to have been used in at least 2000 attacks targeted against various industrial sectors, particularly the energy sector, such as Electric Power Plants in the United States and Europe. Once installed, Havex scanned the infected system to locate any SCADA or ICS devices on the network (ICS = Industrial Control System, like PLC, DCS or SCADA) and sent the data back to command and control servers. To do so, the malware used OPC and collect information such as CLSID key, server name, Program ID, OPC version, vendor information, running state, group count, and server bandwidth.
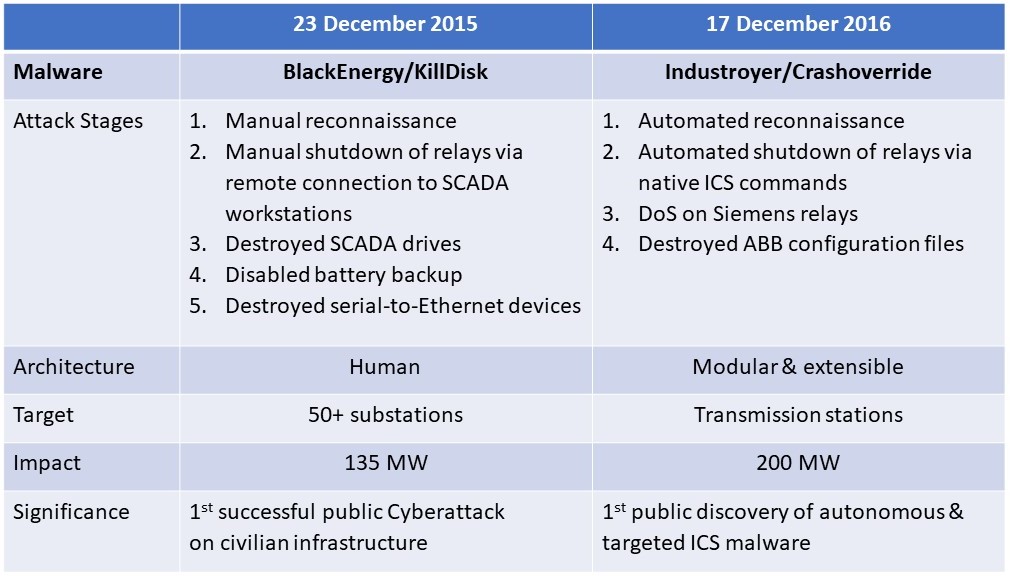
2015 BlackEnergy, also called KillDisk (A):
Was an attack to the Ukraine’s power grid and caused a shutdown of Ukraine’s power grid and temporarily disrupt electricity supply to the end consumers by remotely switching off substations. BlackEnergy Malware was first reported in 2007 that generated Distributed Denial-of-Service (DDoS). In 2010, BlackEnergy 2 appeared with capabilities beyond DDoS. In 2014, BlackEnergy 3 came equipped with more functionality and a variety of plug-ins. A Russian-based cybergang known as Sandworm is recognised with using BlackEnergy attacks. The attack is distributed via an Email attachment being a Word document or PowerPoint file, trapping victims into clicking the apparently normal file.
2015 PLC-blaster worm (A):
Programmable Logic Controllers (PLC) and used in industry to control the process and are nowadays equipped with Ethernet ports and can communicate using TCP and IP-addresses, as used in Internet technology. A lab-worm was created in 2015 by researchers from OpenSource Security to prove that PLC worms can seriously threat a PLC. The PLC blaster worm was specifically designed to attack SIMATIC S7-1200 v3 controllers. This worm does not require any additional PCs to spread to other PLCs. The worm lives and runs only in the PLC. The worm scans the network for new targets (other PLCs), attacks these targets and replicates itself onto the targets found. The worm creates a DDoS attack and luckily was never out in the open.
2016 Industroyer, also called Crashoverride (A):
Industroyer (also referred to as Crashoverride) is the second generation of malware used in the cyberattack on Ukraine’s power grid on 17 December 2016. A fifth of Kiev, the capital of Ukraine, was cut off power for one hour and is considered that this was just a large-scale practical test. This was the second Cyberattack on Kiev in two years. Again, it used remote controls and OPC to get controls over IACS systems and also erased system-crucial Registry-keys and overwrite files to make the system unbootable, i.e. not able to restart. See also 5.7 Types of malware, for a comparison of the first generation and the second generation of attacks on the Ukraine’s power grid.
2016 Shamoon 2 (A):
On the 2nd of Dec 2016, 4 years after the first attack, the same happened again to Saudi Aramco called Shamoon 2 with disk-wiping malware, slightly modified, return of the Disttrack Wiper. Since late November 2016, the Shamoon 2 attack campaign has brought three waves of destructive attacks to Saudi Arabia. Shamoon 2 also wipes data and takes control of the computer’s boot record, which prevents the PC from being turned back on. According to security experts, the actor behind the Shamoon attacks was likely the Iranian government.

2017 WannaCry (A):
WannaCry was a ransomware attack on 12 May 2017. It was caused by a ransomware Crypto-worm using the Microsoft Windows operating system (OS) by encrypting data and demanding ransom payments in the Bitcoin Cryptocurrency. The attack was estimated to have affected more than 250,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of US Dollars. According to Kaspersky Lab, the four most affected countries were Russia, Ukraine, India and Taiwan in the first day.
2017 Petya Goldeneye (A):
Petya (named after the weapon satellite in a James Bond movie Goldeneye) is a family of encrypting ransomware, first discovered in March 2016 and targeted Windows-based systems. On 27 June 2017, a major global cyberattack began, named NotPetya (to distinguish it from the 2016 variants), with infections in France, Germany, Italy, Poland, United Kingdom and the United States. However, most infections were targeting Russia and the Ukraine. Initially more than 80 companies were attacked, including the National Bank of Ukraine. The targets in these countries were mainly Energy Companies, the power grid, bus stations, gas stations, the airport and banks. Around that period other variants (mutant versions) were launched as well called Red Petya, Green Petya, Mischa and PetrWrap, using one of the most advanced cryptographic algorithms around, it also encrypts the entire hard drive by overwriting the master reboot record, to lock the system in order to prevent the computer from loading the OS again. Goldeneye is distributed by phishing e-mails, probably from a German native speaker, called Janus Cybercrime Solutions. WannaCry, Petya GoldenEye and NotPetya are using the same vulnerability from the NSA leaks called EternalBlue.
2018 Triton (PS, I and A):
Triton (also called TRISIS) is an ICS Attack Framework and has caused operational disruption to critical Infrastructure. The attacker (most probably the Russians again, called Xenotime) have developed the capability to cause physical damage and as a result the shutdown of operations of a Petrochemical company in Saudi Arabia, at Saudi Aramco. The malware gained remote access to a SIS Engineering Workstation and deployed the Triton Attack Framework to reprogram the Triconex SIS, the Safeguarding Systems of oil production facilities. Luckily a mistake was made by the attackers in the attack framework that cause the facilities to shutdown on a diagnostic failure message. Triton is seen as the first direct attack on SIS, the integrity heart and last line of defence of production facilities. Xenotime, Hacking Group behind Triton, found probing Industrial Control Systems (ICS) of Power Grids in the US in 2019.
2018 Xbash (A):
Some people recommend to change to another operating system, such as Linux, but new attacks, like Xbash ransomware, attacks both Linux and Microsoft Windows servers. Xbash was discovered by Palo Alto Networks in September 2018 and it combines a Botnet, Ransomware and Coinmining in one worm, so it is a multipurpose worm. Xbash has self-propagating capabilities that means that it has worm-like characteristics like WannaCry. Linux is also used in Industrial Applications and is therefore also a candidate of being attacked.
2019 LockerGoga (A):
“OSLO (Reuters) – Norske Hydro, one of the world’s largest aluminium producers, has made some progress restoring operations but is not yet back to normal after it was hit on 18-03-2019 by a ransomware Cyber-attack”, the company said on Wednesday, 20-03-2019. The attack, LockerGoga malware, is the most active ransomware. It focuses on targeting companies and bypass AV signature-based detection. It loads, using the company’s own Active Directory services, a malicious file on the system to the ‘%TEMP% directory’ from an infected Email attachment and progresses to the OT, where it infects PCD-systems.
2021 DarkSide (PS, I and A):
DarkSide is a cybercriminal hacking group, believed to be based in Russia, that targets victims using ransomware and extortion. It is believed to be behind the Colonial Pipeline cyberattack. It is thought that they have been able to hack and extort money from around 90 companies in the USA alone. The group provides Ransomware as a Service (RaaS). DarkSide itself claims to be apolitical.
DarkSide is believed to be based in Eastern Europe, likely Russia, but unlike other hacking groups responsible for high-profile cyberattacks it is not believed to be directly state-sponsored (i.e., operated by Russian intelligence services). DarkSide avoids targets in certain geographic locations by checking their system language settings. In addition to the languages of the 12 current, former, or founding CIS countries the exclusion list contains Syrian Arabic. Experts state that the group is “one of the many for-profit ransomware groups that have proliferated and thrived in Russia” with at least the implicit sanction of the Russian authorities, who allow the activity to occur so long as it attacks foreign targets. The language check feature can be disabled when an instance of ransomware is built. One such version was observed in May 2021. Additionally, DarkSide does not target healthcare centres, schools, and non-profit organizations.
Ransomware code used by DarkSide resembles ransomware software used by REvil, a different hacking group; REvil’s code is not publicly available, suggesting that DarkSide is an offshoot of REvil or a partner of REvil. DarkSide and REvil use similarly structured ransom notes and the same code to check that the victim is not located in a Commonwealth of Independent States (CIS) country.
From December 2020 to May 2021, ransoms demanded by the group ranged from US$200,000 to US$2 million. DarkSide attacked U.S. oil and gas infrastructure on four occasions. DarkSide ransomware hit the IT managed services provider CompuCom in March 2021, costing over US$20 million in restoration expenses; it also attacked Canadian Discount Car and Truck Rentals and Toshiba Tec Corp., a unit of Toshiba Corp. DarkSide extorted money from the German company Brenntag. The cryptocurrency security firm Elliptic stated that a Bitcoin wallet opened by DarkSide in March 2021 had received US$17.5 million from 21 Bitcoin wallets (including the Colonial Pipeline ransom), indicating the number of ransoms received over the course of a few months. Elliptic’s analysis showed that in total, Darkside received over US$ 90 million in ransom payments from at least 47 victims. The average ransom payment was $1.9 million.
2022 BlackCat (A)
First detected in November 2021, BlackCat (also called AKA ALPHV, Noberus) is regarded as one of the most sophisticated and threatening malware strains of 2021 and 2022. However, BlackCat’s blitz campaign peaked in late-2022 with a 28 percent drop in recorded infections. BlackCat is the first prominent malware written in the Rust programming language, a new language whose popularity is increasing due to its high performance and memory safety. BlackCat also boasts another capability: it can compromise Windows- and Linux-based operating systems.
BlackCat is operated as a ransomware-as-a-service (RaaS) by ALPHV, a Russian-speaking group of cybercrime actors. Its campaigns often employ a triple-extortion tactic: making individual ransom demands for the decryption of infected files; for not publishing stolen data; and for not launching denial of service (DoS) attacks. Having compromised roughly 200 enterprise organizations between November 2021 and September 2022, BlackCat has most often targeted companies in the financial, manufacturing, legal, and professional services industries, but BlackCat’s exploits span all industries.
BlackCat is related to ransomware variants BlackMatter and DarkSide regarding its source code and users. BlackCat operators advertise the ransomware to potential affiliates in private forums, such as the darknet forums XSS, Exploit Forum, and RAMP5, where they look for new cybercriminals to join their ranks.
2022 Pipedream (A)
Recently, the industrial cybersecurity firm Dragos reported on a development that puts industrial installations at even higher risk. According to the report, in 2022, the Chernovite threat group created Pipedream, a new modular malware designed to attack industrial control systems (ICS). This powerful toolkit has the potential for disruptive and destructive attacks on tens of thousands of crucial industrial devices. The risk impacts entities that are responsible for managing the electrical grid, oil and gas pipelines, water systems and manufacturing plants.
Chernovite developers created Pipedream, a modular ICS attack framework that is now the seventh known ICS-specific malware, according to the Dragos report. Pipedream is the first ever cross-industry disruptive and destructive OT-malware. Dragos states that the Chernovite group possesses a breadth of ICS-specific knowledge beyond what’s observed in other threat actors. The ICS expertise demonstrated in Pipedream includes capabilities to disrupt, degrade and potentially destroy physical processes in industrial environments.
While Pipedream itself is a new ICS capability, its appearance reveals a trend toward more technically capable and adaptable adversaries targeting ICS/OT, as per Dragos. In addition to implementing common ICS/OT-specific protocols, Pipedream improves upon techniques from earlier ICS malware. Threat groups such as Crashoverride and Electrum exploited the OPC Data Access (OPC DA) protocol to manipulate breakers and electrical switchgear. Meanwhile, Chernovite uses a newer but comparable OPC UA protocol. Dragos has high confidence that a state actor developed Pipedream intending to leverage it for future disruptive or destructive operations. Pipedream’s capabilities provide an adversary with a range of options for learning about a target’s OT network architecture and identifying its assets and processes. This information lays the groundwork for further disruptive and destructive attacks. It also increases an adversary’s knowledge to develop more capabilities to wreak havoc on a much broader scale.
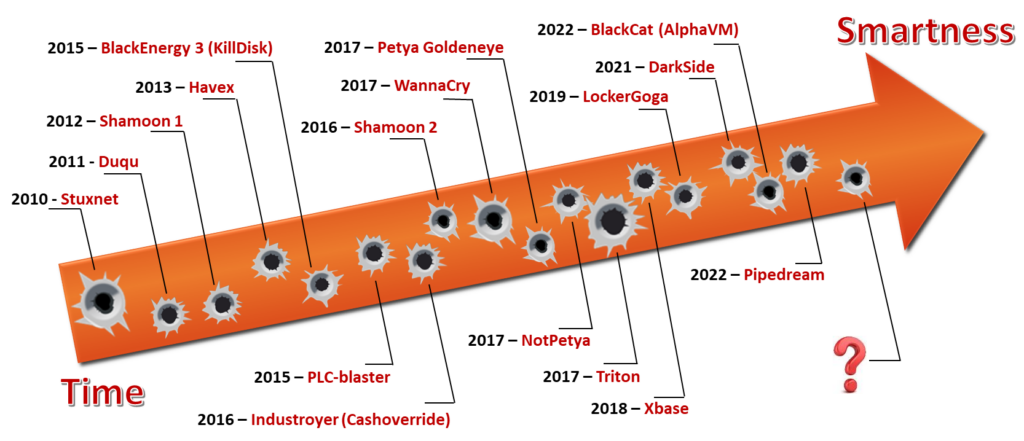
It is evident when looking at the above list of successful hacks and attacks that a well-managed Firewall, up-to-date Anti-virus Definition files (AV) and applying the latest patches is not good enough to protect you against focused attackers. AV and Patching are always lacking behind and zero-day attacks will not be stopped!
Malware and attacks are evolving to smarter attacks, more focussed and more automated attacks. A good example is a comparison by Prof. Sandro Etalle, Technical University Eindhoven that showed that the Industroyer/Cashoverride attacks (2016) are much smarter than the BlackEnergy/KillDisk (2015) attacks and is more automated.
There are many different Cyberattacks and depending on its objective can be split in the following types:
- Indiscriminate attacks, do not seem to discriminate between governments and companies
- Destructive attacks, inflict damage on specific organisations
- Cyberwarfare, politically motivated destructive attacks aimed at sabotage and espionage
- Government espionage, stealing information from/about governments
- Corporate espionage, stealing confidential data from corporations
- Stolen e-mail addresses and login credentials, hacking purposes
- Stolen credit card and financial data, create financial benefit
- Stolen medical-related data, to be sold on the black market
- Hacktivism, to promote a political agenda or a social change to enforce free speech and human rights
It is evident when looking at the above list of successful hacks and attacks that a well-managed Firewall, up-to-date Anti-virus Definition files (AV) and applying the latest patches is not good enough to protect you against focused attackers. AV and Patching are always lacking behind and zero-day attacks will not be stopped easily!